Replacing SSL certificates with certificate management tools
Anyone who wants to make a homepage secure uses an SSL certificate for this purpose. A price comparison for SSL certificates is worthwhile. However, not only SSL encryption causes costs. The time needed to request, set up and monitor certificates should also be taken into account. Then there is the time needed to renew the server certificate. If you have many certificates in use at different locations, it is worthwhile to have the support of a certificate management tool. We give you tips and advice on choosing the right tool.Contents
Which SSL certificate do I need?
Tasks of digital certificates
Why certificate management?
Possible sources of error and risk factors
Advantages of certificate management tools
What should be considered when choosing a certificate management tool?
How do you go about finding the right tool?
For whom are free tools suitable?
Who needs a professional tool?
Why do I have to pay for professional tools?
What are the arguments in favour of essendi xc?
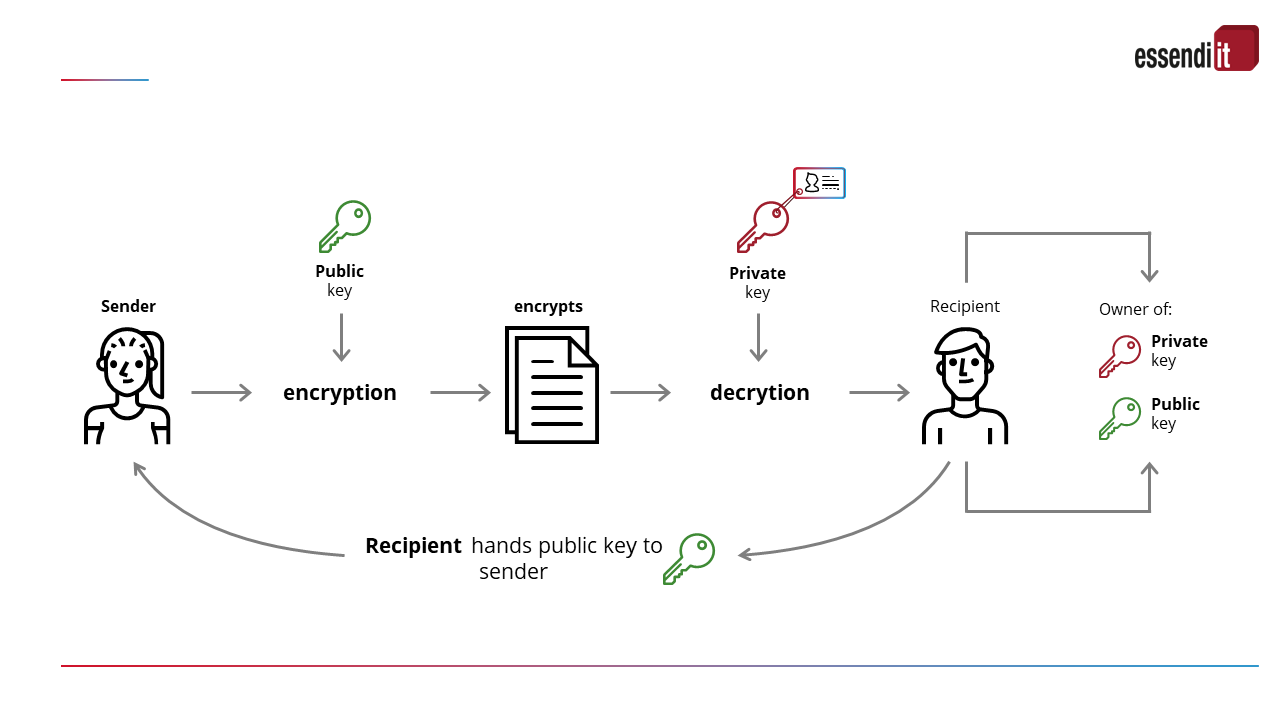
Certificates can be compared to an identity card or passport. They contain the name and the public key of the owner. This makes it possible to identify him or her unmistakably.

 Which SSL certificate do I need?
Which SSL certificate do I need?
Certificates are issued by a trustworthy authority, the certification authority (CA). For this purpose, they are signed with the private key of the CA.
There are different types of SSL certificates, they cost differently depending on their characteristics.
- DV certificates (Domain Validation)
These are the most commonly used SSL certificates. They can be obtained from various certification authorities, including Let’s Encrypt. Before the certificate is issued, a machine checks whether the DNS entry of the website is actually in the name of the applicant. The identity of the owner is thus checked.
- OV certificates (Organisation Validation)
Organisation-validated certificates represent the next highest security level. In addition to the domain, an identity check is carried out. For this purpose, a register entry (e.g. from the commercial or association register) and contact details must often be submitted.
- EV Certificates (Extended Validation)
Especially large organisations with high security requirements use EV SSL certificates with extended validation. It offers the highest level of security through a multi-stage identity check. This is particularly important for large web shops or banks. Since various documents have to be presented, validation can take up to two weeks.
- S/MIME certificates (e-mail validated certificates)
An S/MIME certificate (Secure/Multipurpose Internet Mail Extensions) is used to encrypt and sign e-mails. The key pair it contains is used for asymmetric encryption.
The private key always remains with the certificate holder, the public key is communicated to the communication partners. Outgoing mails are encrypted with the private key. Incoming mails that have been encrypted by the sender with the public key are decoded with the private key.
Special feature: If the private key is located directly in the mail programme (and not on a gateway server), encryption takes place end-to-end. This ensures the highest level of confidentiality.
- Wildcard certificates
A wildcard certificate protects not only the main domain, but also subdomains. Subdomains can be recognised by a dot in front of the domain name. For example, xc.essendi.de is a subdomain of essendi.de.
- Root certificates
A root certificate is signed directly by the certification authority. They are therefore also called self-signed.
 Tasks of digital certificates
Tasks of digital certificates
A distinction is made between authentication and infrastructure certificates for different areas of application. There are certainly more use cases than the following examples.
- E-mail signatures
E-mails are usually signed using S/MIME certificates. This protects the messages from access by third parties. At the same time, the senders can be clearly verified.
- Electronic signatures / electronic seals
Electronic signatures and seals belong to the category of electronic trust services. The Trust Services Act (formerly: Signature Act) distinguishes between two types of trust services.
Qualified electronic signatures for natural persons can replace analogue signatures. They are always used when mobile and yet legally secure signatures are required (e.g. when terminating a contract).
Electronic seals for legal persons correspond roughly to the stamp of a company or a public authority. They can be found as digital proof of authenticity, e.g. under official notices.
- Electronic time stamps
Qualified electronic time stamps can be used to sign documents that must be issued on a certain date or at a certain time. This is the case, for example, for the timely submission of bids in tenders.
All these trust services are issued by qualified trust service providers such as Deutsche Telekom.
- Securing websites
Websites are protected with SSL/TLS certificates. This can be recognised by the closed lock symbol in the browser line. Data that is entered into a web form on the site in the case of an order is transmitted in encrypted form. As the domain owner, you must regularly renew the website certificate before it expires.
- System authentication
System authentication uses certificates to identify a user, computer or device. Without a matching certificate, no access is granted to devices, networks, VPN or applications (even on partner systems). Certificate-based authentication can be used for all endpoints, whether for people, computers or IoT devices.
- Machine communication (M2M communication)
If devices are to communicate with each other, they must be equipped with corresponding machine certificates. They provide each machine with a unique identity. With this, it can identify itself to other machine or personal identities and systems in the network.
This ensures that only authorised machines can access certain data. At the same time, communication between the machines is protected.
 Why certificate management?
Why certificate management?
Digital certificates always contain the name and the public key of the owner. This makes it possible to uniquely identify the owner. Certificates are therefore an essential building block for trust on the internet. However, since they only have a limited validity, they must be closely monitored.
The more certificates there are in a network, the more difficult it is to monitor them manually.
Identities are defined by the keys anchored in the certificates. They can also be used to control authorisations and access to sensitive data. Careful certificate management is therefore also important in order to keep an eye on certificate-dependent authorisations and to be able to change them if necessary.
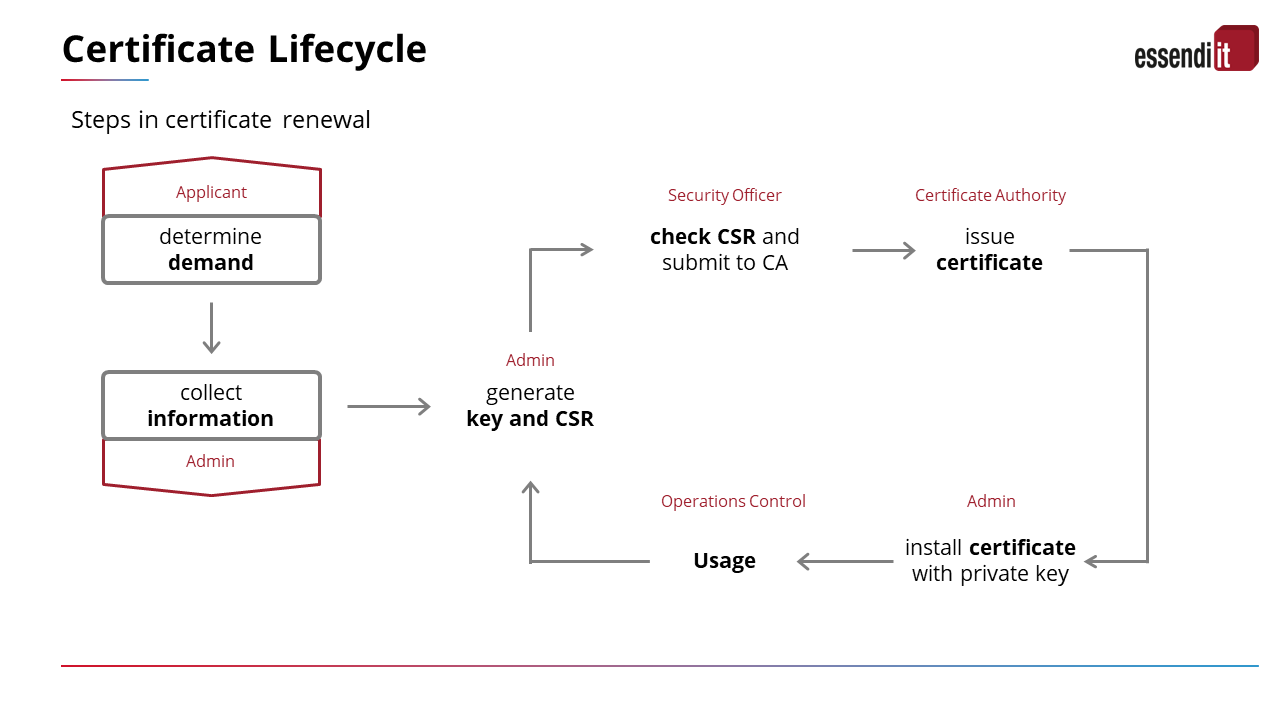
In large companies, there are often several thousand certificates in use. They all have to be kept in view and renewed in time. Critical infrastructure companies in particular must therefore rely on reliable tools. Such a tool can help minimise errors in the entire certificate life cycle.
 Possible sources of error and risk factors
Possible sources of error and risk factors
Incorrectly configured certificate
When applying for a certificate, sufficient key lengths, internal compliance specifications and requirements on the part of the CA must be taken into account. If the latter are not observed, the application can be rejected by the CA. Delays may occur due to the necessary reapplication.
Incorrectly installed / uninstalled certificate
Certificates are not always distributed cleanly to the target devices. It can happen that a certificate was requested but not installed or installed on the wrong device.
Incorrectly requested certificate
Especially when certificates are not applied for automatically according to defined specifications, errors can occur during the application process. If authorisation is controlled via certificates, users may be assigned rights that are too extensive or too severely restricted.
Undetected certificates in the network
Some devices or applications bring their own certificates into the network unnoticed. You only notice that they have expired when the device or application no longer functions. Often, however, the cause of the error must first be searched for.
In all the cases mentioned above, communication may no longer be established. Processes come to a standstill. This can lead to financial losses and loss of reputation. Therefore, certificate management is an absolutely necessary task.
 Advantages of certificate management tools
Advantages of certificate management tools
No system failures due to expired certificates
Probably the most important advantage is that certificate management tools prevent unnoticed expired certificates and thus system failures.
Time savings
Automated tools take over many steps of certificate management. This relieves IT security administrators. Their working time is freed up for other tasks.
Centralisation
Certificate management centrally from one point simplifies processes.
Standardisation
Clearly defined application processes and standardised user profiles (roles) minimise sources of error and thus the risk of incorrectly applied for certificates.
Reporting
Management reports provide a concentrated overview of the certificate inventory. Some tools also offer special compliance reports for audits.
Altering
Some tools warn when certificates are about to expire, reminding users to reapply and install them in good time.
Enhanced security
Defined application processes and authorisations, compliance requirements and installation routines minimise sources of error. This ensures a secure network.
 What should be considered when choosing a certificate management tool?
What should be considered when choosing a certificate management tool?
If you decide to use a tool-supported certificate management, you should pay attention to the following points:
| Scalability To which extent can the tool be adapted to the company’s requirements and compliance specifications? |
Interfaces (vendor independence) Do I commit to a fixed CA or PKI when choosing a particular tool? Can I switch to an alternative CA / PKI if necessary? |
|
| Possible degree of automation How much work can the tool do for the staff? For example, can it also deliver certificates to the target systems? |
Support quality, accessibility Can the management software vendor provide sufficient support for the company’s requirements? Is it easy to reach or can difficulties arise due to different time zones? Is there a hotline for after-hours or weekend emergencies? |
|
| Quantity of destinations in automatic distribution Networks consist of a multitude of servers, devices, cloud components, IoT devices, etc. They all need certificates and the more that can be automatically provisioned, the better. |
Operable as a service In some cases, it may make sense to use the application as a managed service. This saves the system administrators additional work. |
|
| Possibilities for extending the range of functions Can additional features such as CT log monitoring or a scan function be added later? |
Competence of the manufacturer Has the manufacturer been on the market for a long time and does he have experience in different sectors and use cases? |
|
| Usability In a network, many different communication partners come together. Can all existing systems be connected to the tool? |
Roadmap Is there information on how long the product will be supported? Are there regular further developments and releases? What is the strategic relevance of the product for the manufacturer? |
|
| Can it be integrated precisely into heterogeneous infrastructures? How much work can the tool do for the employees? For example, can it also deliver certificates to the target systems? |
 How do you find the right tool?
How do you find the right tool?
Even before you start looking for possible certificate management tools, you should carry out a needs and requirements analysis. In order to avoid a potentially costly switch to a larger tool later on, one should take the time to carefully define must and can criteria. Some examples are:
- Which use cases exist in the company?
- Which ones absolutely have to be covered?
- Which ones can be automated with existing tools (e.g. Microsoft PKI / MS PKI)?
- How many users need to access the tool? Only 5 admins or 30,000 end users?
- What are the industry-specific requirements for operation and access?
- Do certain compliance requirements have to be observed?
- How much has the number of required certificates grown in the past? Based on this, the likely number needed in the future should be estimated.
We have provided a comprehensive list of selection criteria for you to download free of charge.
 For whom are free tools suitable?
For whom are free tools suitable?
For private users and companies that only need to manage a handful of certificates, “manual monitoring” with spreadsheets and calendar entries is often sufficient. In the spreadsheet, the framework data such as issuing CA, place of use and required characteristics are recorded. An appointment entry in the calendar reminds of the timely renewal.
As the complexity of the network increases, so do the requirements for certificate management. Particularly in the open source area, there are a number of free tools that offer a little more comfort than table and calendar.
Certificate management with spreadsheet and calendar
| Advantages | Disadvantages |
| + Overview of certificate inventory | – Only monitoring, no automation of processes |
| + Spreadsheet and calendar already at hand | – Becomes confusing with large number of certificates |
| + Functions known | – Offers no additional functions |
| + Free of charge |
Disadvantages of free tools
Limited range of functions
Free tools offer fewer functions than paid tools. It is therefore worthwhile to check whether the chosen application includes all the must-have criteria.
Limited support, no warranty
Some free software was developed by users to solve a problem in their own network. Afterwards, the application was made available. If one chooses such software, there is no warranty for the application. Also, if there are problems with the software, there is little or only slow support.
If you use open source software, you can contact the open source community via forums if you have problems. However, it can take longer to find the right solution. Alternatively, companies also offer support and supplementary services for open source software. However, these are then subject to a charge.
Limited or delayed support for incidents
With a free tool, there is no SLA (Service Level Agreement) to guarantee certain performance standards and qualities in the event of an incident. This means that there is no fixed contact person available to provide help as quickly as possible with competent solutions. Again, one is dependent on one’s own knowledge, the open source community or external service providers.
No individual adaptations
Free tools are available “as is”. Customisations tailored to the company may have to be developed by oneself. Again, there is the option of seeking help in appropriate forums or having the desired add ons programmed for a fee. Here, too, the time factor must not be neglected.
No regular releases or updates regarding technical innovations
Especially applications that have been developed for personal use are only further developed if there is a corresponding personal need. For them, there may be no regular updates with updates regarding technical innovations.
These may have to be carried out by the user or requested in forums or from a service provider.
No certainty regarding ISO conformity
Depending on the scope of functions, the selected tool may not be designed to take into account certain compliance requirements.
Free tools are therefore less suitable for very complex infrastructures. On the one hand, the decision depends on the complexity of the use cases and the certificate volume. In a closed framework, an MS PKI works and you don’t need a big tool.
On the other hand, they require corresponding prior knowledge or familiarisation with the topic. If neither is available, the corresponding maintenance costs should be taken into account.
Certificate management with open source tools or free basic tools
| Advantages | Disadvantages |
| + Overview of certificate inventory | – Limited or highly specialised range of functions |
| + Free of charge | – Additional functions must be developed by the user or are subject to an additional charge |
| + Download and install yourself | – Requires training on your own |
| – No or only limited and time-delayed support | |
| – Often depending on a specific CA |
 Who needs a professional tool?
Who needs a professional tool?
Companies that use a large number of certificates need a professional certificate management tool for volume and mass handling. Not only the quantity of certificates is important, but also how many users, peripheral systems and target devices have to be supplied. In addition, the following and (depending on the company) other questions should be asked:
Do expired certificates threaten the failure of critical processes?
If critical company processes or production are affected by an expired or faulty certificate, it must be possible to monitor it continuously.
How high is the level of protection / compliance?
How interesting is the company data or customer data stored in the company for potential attackers? The higher the level of protection, the stricter the crypto guidelines should be.
What risks does a process failure represent?
Does a process failure possibly mean that important applications cannot be made available (stock exchange trading platforms, ATMs, power supply, …)?
How is the availability of applications ensured?
The fact that an infrastructure runs cleanly can only be guaranteed via a tool containing an SLA. This agreement regulates, among other things, to what extent and how quickly support is available. With an SLA, both sides can be sure to have a reliable partner at their side.
Certificate management with fee-based tools
| Advantages | Disadvantages |
| + Overview of the certificate inventory | – Subject to costs |
| + Alerting function | – Not all are manufacturer-independent (regarding HSM, smart cards, …) |
| + Authorisation control | – Not all are CA-independent |
| + Customer service / support | – Large manufacturers often do not offer customisation |
| + Regular updates and releases |
 Why are professional tools fee-based?
Why are professional tools fee-based?
Professional certificate management tools require a great deal of development and know-how. Since they have to be precisely tailored to the respective company, you receive extensive support during their introduction. And because they manage cryptographic material, they must always be up to date with the latest security standards. Releases are developed regularly for this purpose.
For these reasons, setup and other running costs are incurred in addition to the licence fees for the software.
Nevertheless, it is worthwhile weighing up whether to develop such a tool yourself or to fall back on a ready-made application that can be adapted exactly to one’s own requirements with add-ons.
Each kind of software has its own individual merits. During the selection process, make sure that the must-have criteria you have defined are covered. It is an advantage if your nice-to-have criteria can be integrated quickly and easily at a later stage.
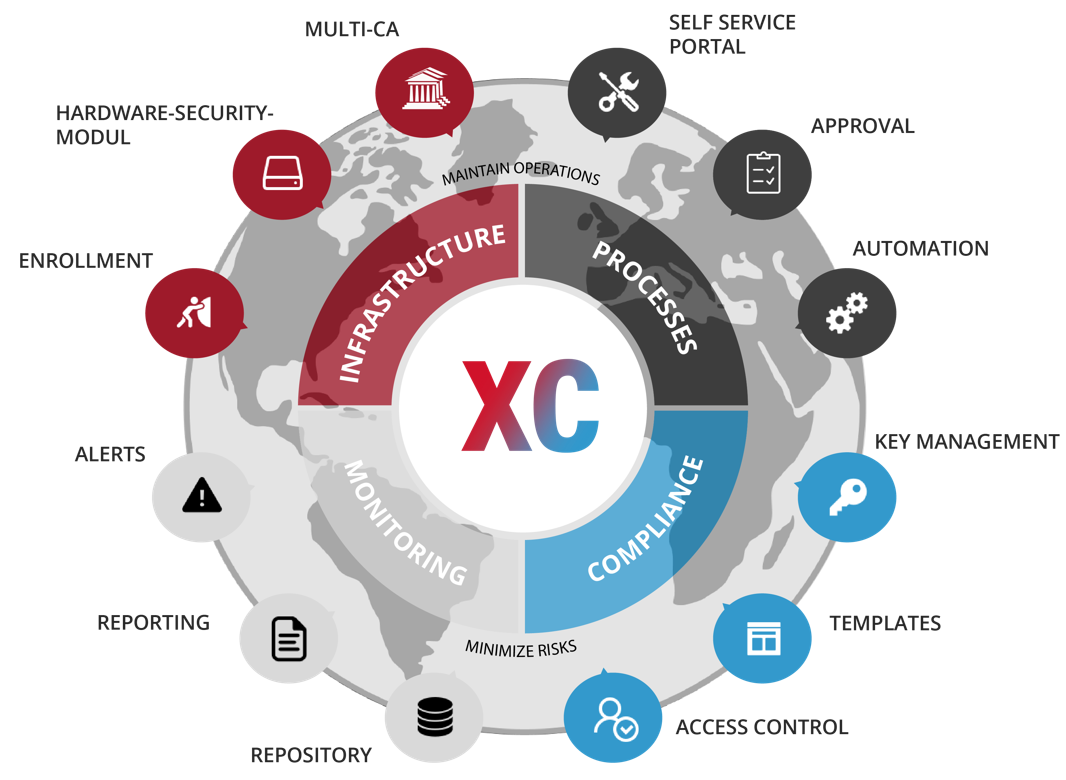
What are the arguments in favour of essendi xc?
In addition to the advantages mentioned above, xc offers the following benefits:
| Advantages | Disadvantages |
| + Vendor independence (HSM, Smart Cards, …) | – Fee-based |
| + CA-independent | |
| + Multi-PKI | |
| + Data security and data protection (Software made in Germany) | |
| + Fully automated up to the point of deployment into the target systems | |
| + Precise integration into the operating environment | |
| + Individually adaptable / scalable | |
| + Multilingual, personally available support | |
| + Software customisable directly by manufacturer |
essendi xc is
- a mature standard solution that integrates perfectly into the operating environment
- established on the market since 2015
- Multi-PKI and CA-neutral
essendi xc can
- be combined with innovative product extensions (e.g. essendi cd Certificat Scanning and/or CT Log Monitor)
- deliver new software versions directly to the customer’s target environment (continuous delivery)
essendi xc offers
- a self-service portal that allows departments and users to apply for certificates themselves without much prior knowledge. This reduces the workload of the IT department.
- European standards in terms of data security and data protection
- Full automation of all certificate processes, up to and including installation in the target systems
- easy product customisation and adaptation
- intensive implementation support, rapid response, immediate reaction to incidents
- regular updates and releases
- friendly, multilingual customer service, directly available to you
- comprehensive end2end solution packages from a single source
- HSM connection for various purposes (X-Factor-Auth. PKI access, private keys)
- Smartcard management (e.g. intercede) can be integrated individually if required
- Office / Outlook 365 plugin for certificates in the keystores, incl. key recovery
- Onboarding and identification of IoT devices
You can achieve even more security with optional add-on modules such as essendi cd (extended certificate scan). The tool also finds certificates that have entered the network unnoticed. It includes these in the administration and alerting.
Interested? Simply contact us!

