People have always encrypted important messages when they were transported over long distances. In times of digitalisation, the topic is more important than ever, because we transmit sensitive data every day.

Ancient and classical encryption
One of the oldest encryption methods is the scytale from Greece in the 5th century B.C. It consists of a long strip of parchment wrapped around a stick. In order to read the message, the recipient had to wrap the strip around a stick of the same diameter.
Another ancient encryption method is the Caesar cipher. Julius Caesar is said to have used it in the 1st century BC. Each letter is shifted by a fixed number of positions in the alphabet. In the 16th century, the method was extended using a variable shift (Vigenère cipher), making it much more secure.
Enigma, an encryption machine used by the German Wehrmacht during the Second World War, is particularly well known. It consisted of a keyboard and rollers. Each keystroke led to a complex encryption by rotating the rollers. For a long time, this method was considered unbreakable.
Data encryption is still a hot topic today. Every day, we transmit data that we don’t want to fall into the wrong hands: from credit card information and login data to WhatsApp messages. But how exactly does encryption work?
Modern cryptography
Modern cryptography is based on mathematical algorithms. The most important methods of encryption today are symmetric and asymmetric cryptography.
In symmetric encryption, the sender and recipient of the message use the same key. Of course, both must know it. To ensure adequate protection, it must be transmitted unencrypted and separately from the message, i.e. at best in person. Things get really complicated when the number of parties involved increases, but not everyone should be able to read all messages. Then several different keys must be used, which must not be mixed up.
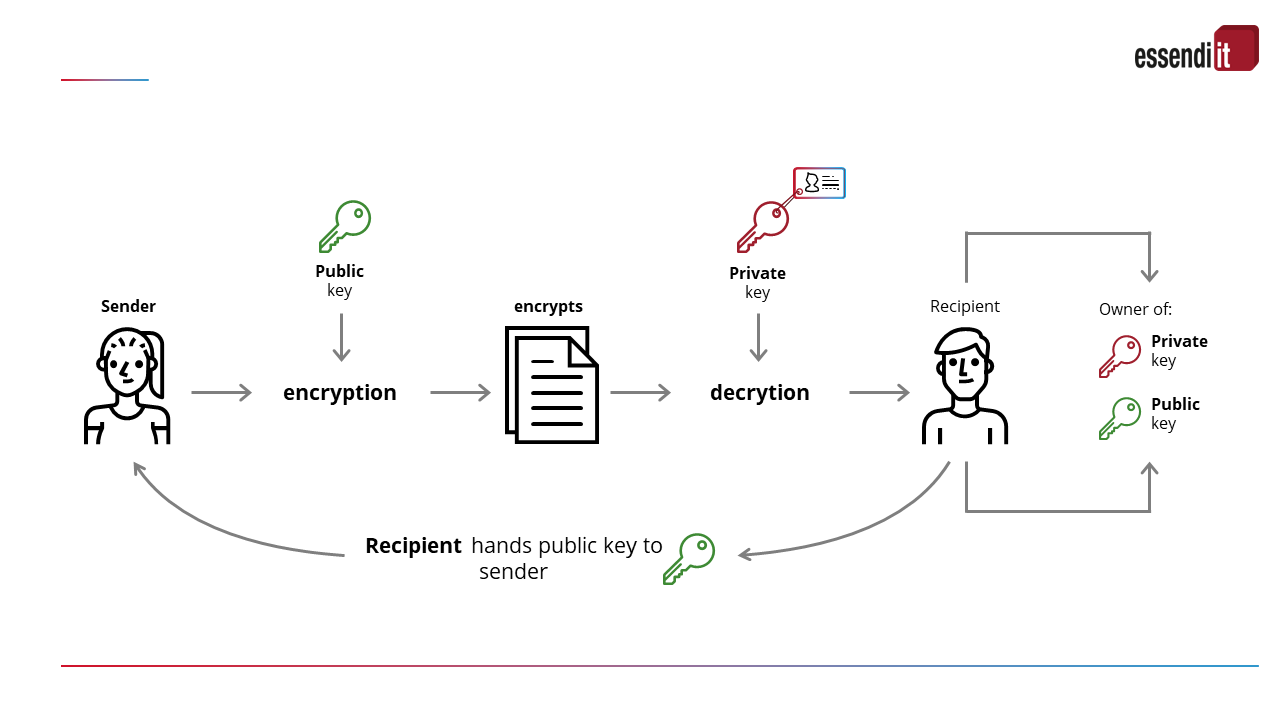
In asymmetric encryption (public key cryptography), a mathematically linked key pair is used: a public key for encryption and a private key for decryption. Each user can send messages with the public key, but decryption is only possible using the private key. This means that only a single key pair is required for each participant.
Well-known algorithms are RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography).
RSA is based on the prime factorisation of large numbers. ECC uses elliptic curves and offers security comparable to RSA with shorter keys, which increases efficiency in resource-constrained environments such as smartcards and IoT devices.
Post-quantum cryptography
Today’s cryptography is under threat from quantum computers. These solve complex mathematical problems in a very short time and break today’s encryption. In post-quantum cryptography, research is therefore being conducted into quantum-resistant algorithms.
Their implementation is a challenge, as the new algorithms must comply with certification standards (NIST) and interact with existing systems. As they require more resources, hardware and software may have to be adapted. Digital certificates also need to be renewed. This requires careful planning to ensure that the certificate infrastructure meets the new requirements. Certificate management tools such as essendi xc provide support and ensure the continuity of secure communication.
We are currently researching the use of algorithms that comply with the latest NIST standards (National Institute of Standards and Technology) in the field of “quantum-safe cryptography” with the Lucerne University of Applied Sciences and Arts.
Cryptography is therefore always used when only the person for whom a message is intended should be able to read it (confidentiality / access protection). In addition, it also ensures the integrity of a message, as the recipient must be able to trust that the message has not been changed since it was created (protection against modification). Authenticity can also be checked and thus the author or sender can be clearly identified (protection against forgery). Last but not least, cryptography also ensures reliability by documenting the originator of the data or message (non-repudiation).
This makes it possible, for example, to create digital signatures or to authenticate oneself in interactive communication.
When it comes to data protection and IT security, cryptography is therefore a top issue.




