When it comes to data security and secure communication on the Internet, there is no getting around the term Public Key Infrastructure (PKI). These three letters are used to describe a network of various participating agencies – in other words, an infrastructure. It is a type of key management and is used to confirm digital identities and encrypt data.
We explain here how it all works and what you need to consider in PKI management. Furthermore, you will learn how you can easily adapt your PKI to the IT security requirements of your company with essendi xc.
Content:
What are the components of a PKI?
How does a Public Key Infrastructure work?
What is a PKI used for?
Who has a PKI?
What is a certificate chain?
What are code signing certificates?
What is the difference between Web Of Trust and PKI?
Why is essendi xc a valuable PKI tool?
What are the components of a PKI?
A public key infrastructure comprises the following components
Public and private keys
Mostly asymmetric cryptographic keys are used. The public and private keys are always generated as a pair and are mathematically linked. In asymmetric encryption, data encrypted with the first key of a key pair can only be decrypted with the corresponding second key.For this purpose, a distinction is made between a public and a private key. The public key is freely accessible to everyone in the network. The private key, on the other hand, is only known to the owner, who does not give it out.
Digital Certificates
Certificates are used in digital communication for authentication, encryption and as signatures. They are composed of various pieces of information. This includes, among other things
- the expiry date of the certificate,
- the digital signature of the issuing certification authority and
- the public key of the certificate owner.
Certificate Revocation List (CRL)
All invalid certificates are entered in the certificate revocation list. A certificate that has been revoked or revoked is invalid, for example, because it has been corrupted or because permissions have changed.
Validation services (Validation Authority)
A validation service (OCSP / CT Logs) checks the validity of digital certificates. To do this, it queries the validity of a certificate from the certification authority by checking the certificate revocation lists, for example.essendi xc also has a validation service, the CT Log Monitor.
Authority (RA)
The registration body works closely with the certification body. It identifies and registers the applicant. It also checks the correctness of the data in the certificate request and then forwards it to the certification body.
Certificate Authority (CA)
The certification authority is the public trust anchor of the PK Infrastructure. It receives the certificate request and issues the requested digital certificate. In doing so, it confirms that the certificate holder really is who he claims to be.It monitors the validity of the certificates it issues and places all invalid certificates on the certificate revocation list.
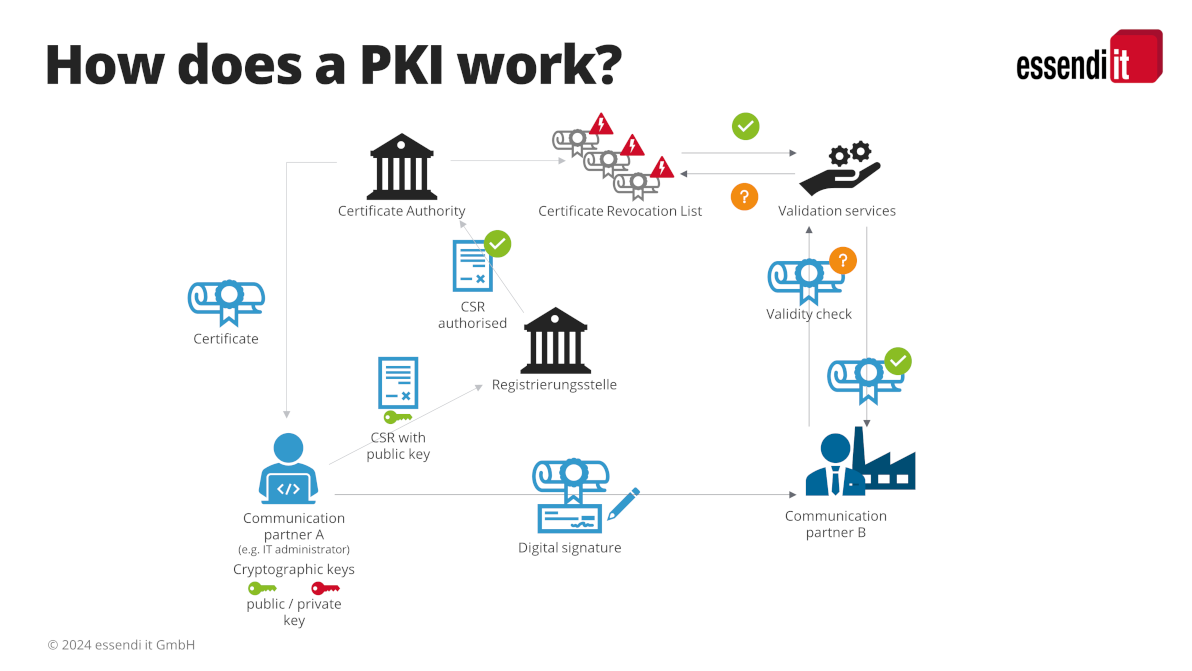
How does a Public Key Infrastructure work?
The functionality of a Public Key Infrastructure is similar to the application for an identity card:
The IT administrator of a company first generates the certificate signing request (CSR) and a cryptographic key pair. He forwards the CSR and the public key to the registration authority. This can be compared to the application form for an ID card, which is submitted to the citizens’ registration office together with a passport photo.
The registration authority checks the CSR and the key. After successful verification, it forwards both to the certification authority (Bundesdruckerei). This in turn then issues the desired certificate (the ID card) (issue certificates) and sends it back to the client.
The IT administrator now installs the certificate together with the private key in the infrastructure of his company. Now the company can identify itself when exchanging information over the Internet and encrypt its data traffic.
What is a PKI used for
The PK Infrastructure uses asymmetric encryption for encrypting and decrypting. The data is encrypted with the public key before it is sent. The recipient can only decrypt it with the private key.
This works for all electronic identities that communicate with a remote station. This includes smartwatches, for example, but also intelligent pacemakers and industrial production facilities.
It is therefore used to protect a wide range of information. It encrypts vital communications such as those between the aircraft and the tower. But it also protects personal data that is transmitted from a smartwatch to an app, for example.
Smart cards also transmit their data securely via a PKI (PKI secured). Smart cards are, for example, key cards for access control and time recording in companies.
We all also know their encryption services from the web browser. The small, closed lock at the beginning of the browser line indicates that data is transmitted securely. Without the lock, the web server will classify the page as “insecure”.
For this purpose, a PK Infrastructure creates, manages, stores, distributes and revokes digital certificates (SSL / TLS / x.509). These certificates confirm the identity of the owner in communication via the Internet. The certificate serves as a kind of ID that you show. You can therefore be sure that the person you are talking to really is who they say they are (authentication).
In addition, web browsers use the keys contained in the certificate to protect the transmitted data from unauthorized access. Only the owner of the private key is able to decrypt the message. This allows a secure connection to be established between the web browser and the web server. This also prevents manipulation of the transmitted data.
PKI e-mail encryption is of particular importance. 80% of all hacker attacks occur via e-mail. Therefore, the most effective method is to send emails encrypted.
Encryption of sent e-mails protects against data theft and modification or manipulation of the contents. This is particularly important when emails contain file attachments with Excel spreadsheets or personal data.
In end-to-end encryption of e-mails, the sender and recipient must know the public key of the communication partner. The sender encrypts its message to the recipient with the recipient’s public key. The recipient can then decrypt and read it with his private key.
In the case of digital signatures (digital signing), on the other hand, the message is signed with the private key. The associated public key confirms the signature.
Who has a PKI?
Basically, everyone who works with encryption methods and certificates needs a PKI. You can set it up yourself and use the Microsoft Public Key Infrastructure, for example, or alternatively use a PKI service provider.
Such a provider, for example SwissSign, provides connection options to a pre-configured Managed Public Key Infrastructure (MPKI).
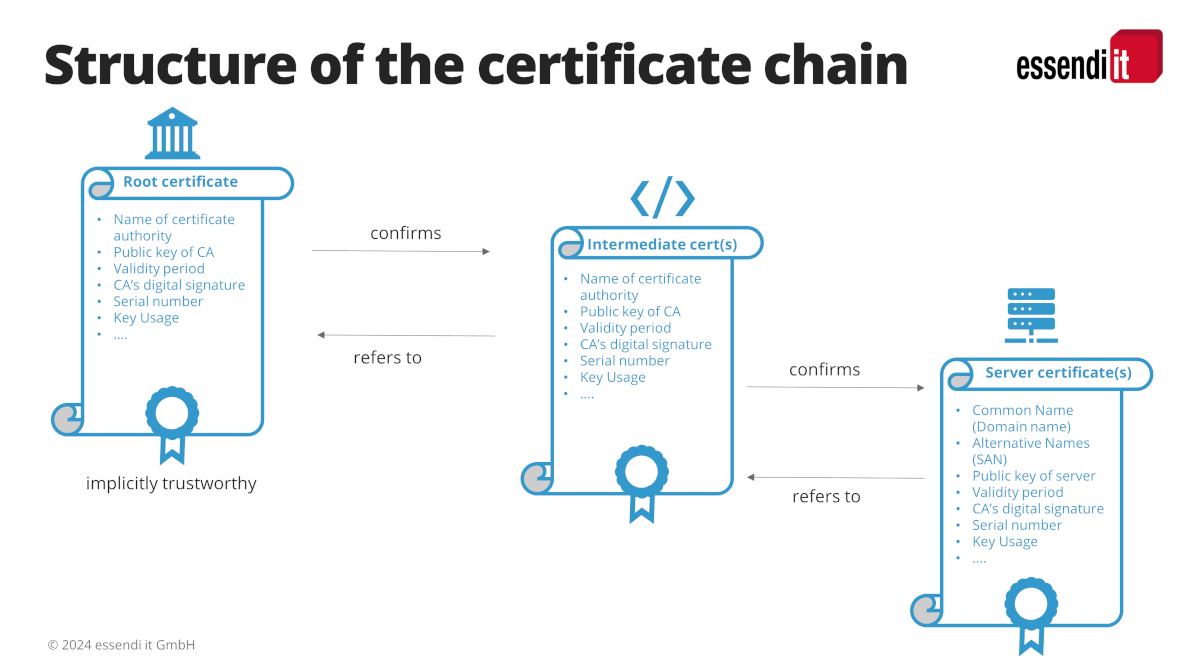
What is a certificate chain?
A certificate chain is the list of all certificates used to confirm a digital identity. The certificate chain always ends at the root certificate issued by the root certification authority (root CA). The root CA is the public trust anchor for all parties participating in a certificate process.
A certificate chain consists of the following components
Root certificate
Root certificates belong to the root CAs and are strictly monitored by them. A root certificate is always signed by the certification authority itself; it represents the root of the trust tree.
Intermediate certificate
In a certificate chain there is at least one intermediate certificate, but often several. The intermediate certificates are the branches of the trust tree. They are the links between the root certificates and the server certificates.
Server certificate
The server certificate is issued specifically for the domain that the user wants to secure.
The chain is only trustworthy if it can be traced back without gaps to its origin – the root. The signatures for all certificates in the chain up to the root certificate must therefore be checked and confirmed. The root certificates of the most important root CAs are already stored in many operating systems or browsers. This makes it easier and faster to trace the certificate chains later.
Errors in the certificate chain therefore lead to problems. A certification path is faulty, for example, when
- no root certificate is included
- the private key is not at the end of the list
- the order of the certificates is not correct
- incorrect or too many certificates are included
- certificates are missing.
What are code signing certificates?
A code signing certificate verifiably confirms who the publisher of a particular software is. The publisher places a digital signature under his application before offering it for download. The code signing certificate shows the user during the download that the software has not been damaged or modified.
Code signing certificates are also issued by certification authorities. As a trust center, they confirm the identity of the programmer or the publisher of the software in this case.
The latter must ensure that the code signing certificate is renewed or extended in due time. Otherwise, the software will no longer be classified as trustworthy. However, the download procedure and also the application itself would still work.
What is the difference between Web Of Trust and PKI?
The Web of Trust (“network of trust”) is an opposite trust model to the PKI. A PKI is hierarchically structured, with the CA forming the central trust anchor. All other instances participating in the PKI trust this root CA. Therefore, the protection of the root CA and the secrecy of its private key is a fundamental prerequisite for a PKI.
In the WOT, on the other hand, all participants jointly confirm the authenticity of digital certificates and cryptographic keys. The more participants confirm (sign) a certificate, the more trustworthy it is. In the Web of Trust, many different participants act as trust centers. They thus replace the CA of the hierarchical PKI model.
Why is essendi xc a valuable PKI tool?
A PKI is a security solution that can be reliably adapted to the respective company’s needs. It must be able to map increasingly complex IT landscapes. That is why the human factor also plays a major role here.
A PKI solution must be set up optimally so that no vulnerabilities arise. There is a lot to consider here and a wide range of expertise is required.
Support is provided by certificate management tools such as the key management software essendi xc. xc acts as a key management system and assists with crypto management. It creates cryptographic keys according to company specifications in the required key length. In doing so, it observes regulatory requirements such as ISO/IEC 27001, BSI Grundschutz or NIST. User errors can thus be excluded.
xc warns in good time before certificates expire. Depending on the setting, it automatically takes over the renewal or extension up to the installation in the target system.
In conjunction with the CT-Log Monitor, it detects forged certificates. If necessary, it can automatically revoke and revoke them.
Manual set up configurations can often only be adapted with a great deal of time and hidden risks. essendi xc, on the other hand, is designed to be flexible from the outset. Therefore, it can be adapted quickly, easily and safely to changing requirements.
Curious about essendi xc? Arrange a live demo here.




